'Cybersecurity 101: How to Protect Your Data From Phishing Attacks' whatisphishing fraudprotection
Scammers use emails or text messages to trick you into giving them your personal information. They may try to steal your passwords, bank account numbers, or Social Security information. If they get that information, they could access your email and bank accounts.
The purpose of phishing is to identify data such as credit card and login information, or to install malware on the victim's electronic device Phishing messages can come in many forms, big or small. There are some types that are more common than others. For example:A particular phishing scam takes the form of a notice that your bank has been suspended due to unusual activity. If you have not opened an account with a bank that sends out such notices, then you won't be affected by this if you are vigilant enough and take the appropriate steps to verify the authenticity of such messages.
Indonesia Berita Terbaru, Indonesia Berita utama
Similar News:Anda juga dapat membaca berita serupa dengan ini yang kami kumpulkan dari sumber berita lain.
 The 101 Best Movie Sequels of All TimeWhether they come after, before, or between their predecessors, these films have their own indelible legacies. Presenting the 101 best sequels of all time
The 101 Best Movie Sequels of All TimeWhether they come after, before, or between their predecessors, these films have their own indelible legacies. Presenting the 101 best sequels of all time
Baca lebih lajut »
 How HackerNoon's New Dynamic Sitemap Improves Story Distribution | HackerNoonThis is the story of how I added a new type of a dynamic sitemap to HackerNoon’s publishing platform to better index our hundreds of thousands of site pages.
How HackerNoon's New Dynamic Sitemap Improves Story Distribution | HackerNoonThis is the story of how I added a new type of a dynamic sitemap to HackerNoon’s publishing platform to better index our hundreds of thousands of site pages.
Baca lebih lajut »
 We Built a Modern Data Stack for Startups | HackerNoonHere's how we built our data stack at incident.io. If you're a company that cares about data access for all, follow this guide and we guarantee great results.
We Built a Modern Data Stack for Startups | HackerNoonHere's how we built our data stack at incident.io. If you're a company that cares about data access for all, follow this guide and we guarantee great results.
Baca lebih lajut »
 Over 35 Tech Companies Compromised in Novel Software Supply Chain Attack | HackerNoonSecurity researcher Alex Birsan breached systems of over 35 tech companies in what has been described as a novel software supply chain attack.
Over 35 Tech Companies Compromised in Novel Software Supply Chain Attack | HackerNoonSecurity researcher Alex Birsan breached systems of over 35 tech companies in what has been described as a novel software supply chain attack.
Baca lebih lajut »
 Bored Ape Yacht Club NFTs stolen in Instagram phishing attackHow to fish $40 million worth of assets? Hack BAYC's Instag
Bored Ape Yacht Club NFTs stolen in Instagram phishing attackHow to fish $40 million worth of assets? Hack BAYC's Instag
Baca lebih lajut »
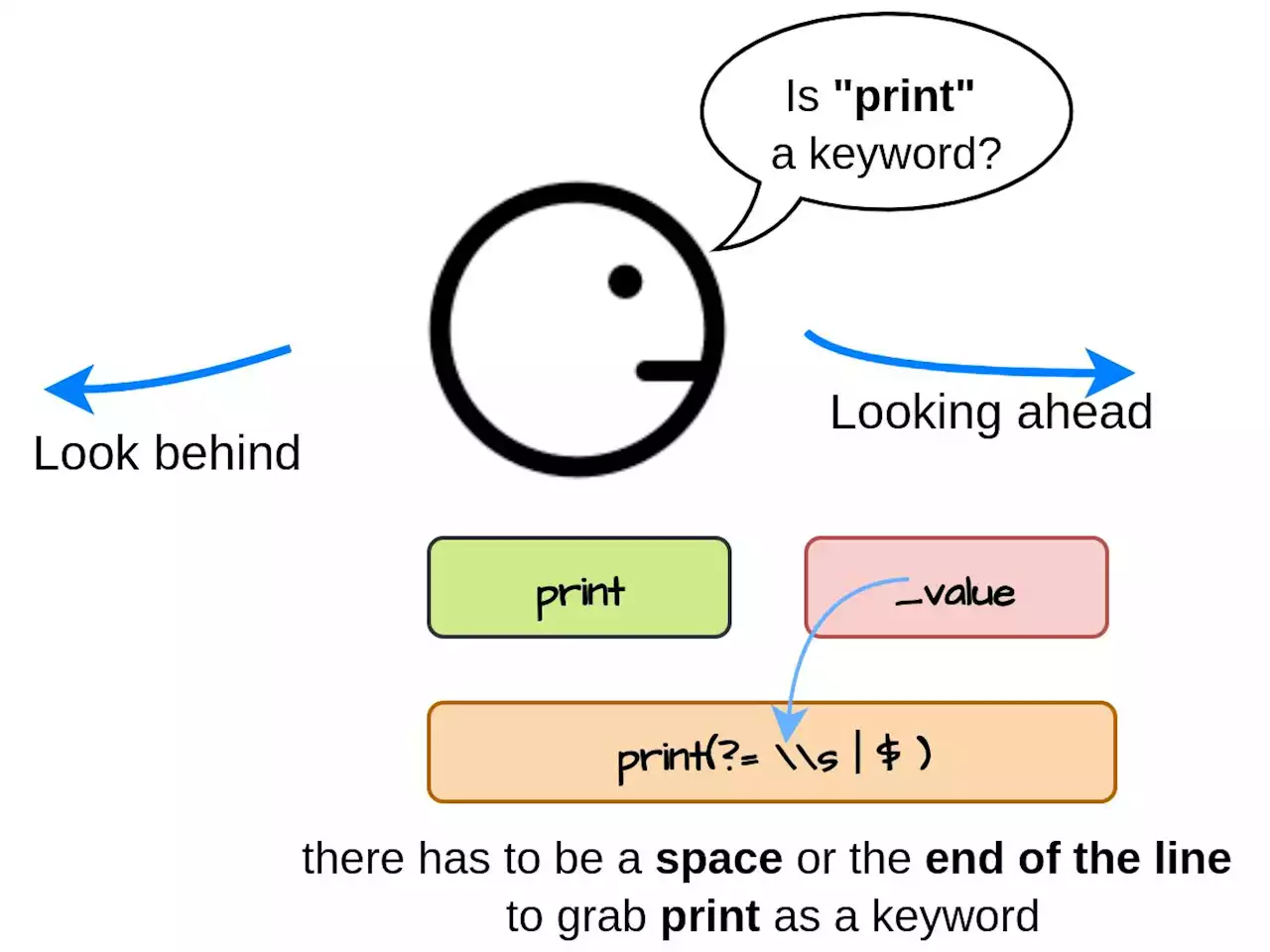 Build Your Own Programming Language Part III: Improving Lexical Analysis with Regex Lookaheads | HackerNoon'Build Your Own Programming Language Part III: Improving Lexical Analysis with Regex Lookaheads' lexicalanalysis regex
Build Your Own Programming Language Part III: Improving Lexical Analysis with Regex Lookaheads | HackerNoon'Build Your Own Programming Language Part III: Improving Lexical Analysis with Regex Lookaheads' lexicalanalysis regex
Baca lebih lajut »
